A new campaign is being recorded in Bynet to send out and infect users of the national segment of the Internet with malicious software (hereinafter referred to as malware). The mailings are aimed at individuals, private and public sector enterprises, as well as law enforcement agencies, state bodies and organizations.
Phishing email
Messages containing malicious links are written in Russian; attackers use a standard social engineering technique using topics that are relevant at the time. Below is a list of topics that attackers used in their mailing lists:
• “Materials – introduction of amendments”
• “Materials for publication”
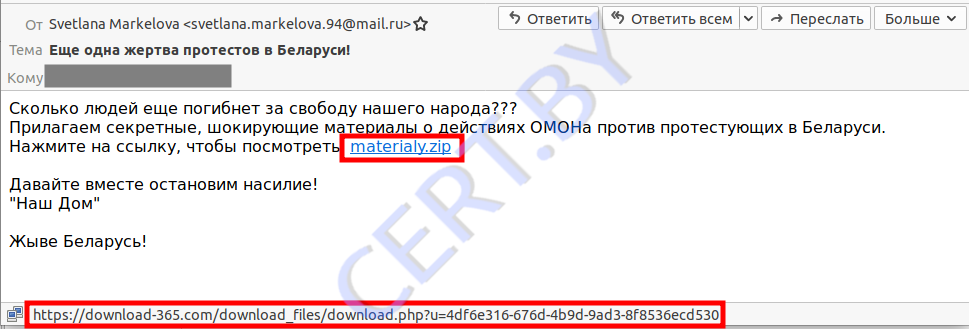
• “Another victim of protests in Belarus!”
Examples of letters with links to download malware are presented below. And one should pay attention to the address to which the transition occurs when you click on the link “materialy.zip”.
Dissimilation
The campaign is aimed at a very large number of users of the national segment of the Internet. Among the recipients of the mailing were individuals, employees of enterprises of the private and public sectors of various fields, as well as law enforcement agencies, state bodies and organizations.
Below is a list of some of them:
• Ministry of Transport and Communications;
• Ministry of Labor;
• State Committee for Property;
• Minsk City Executive Committee;
• National State TV and Radio Company;
• Ministry of Defense;
• and a number of other law enforcement agencies, individuals and legal entities.
During the investigation of these incidents several dozen hosts were identified in our segment of the Internet which are presumably infected with malware distributed in these phishing emails. At the moment users are being notified and information is being checked.
Signs of phishing emails and indicators of compromise
Sender addresses (may vary):
- yulia.matveeva.94@mail.ru;
- andrey.sitak@bk.ru;
- vetlana.markelova.94@mail.ru;
- mariya.novoselova89@inbox.ru;
- ailebedev@inbox.ru;
- sitak.sergey@mail.ru;
- mariya.novoselova89@inbox.ru;
- mdkuznetsov@bk.ru;
- sashabahonovich@tut.by;
- svetlana.markelova.94@mail.ru;
- olga.buzovaa@mail.ru;
- igor.sitak@bk.ru.
URLs:
- hxxps://download-365[.]com/download_files/download.php?u=cf37dafa-939c-412e-a653-d6b01737c870
- hxxps://download-365[.]com/download_files/download.php?u=3b81c594-3700-4056-a1e7-675865b8e4ec
- hxxps://download-365[.]com/download_files/download.php?u=4df6e316-676d-4b9d-9ad3-8f8536ecd530
- hxxps://download-365[.]com/filedownload/download.php?u=cf37dafa-939c-412e-a653-d6b01737c870
- hxxps://download-365[.]com/filedownload/download.php?u=db810273-30b5-4887-894b-ec84e9bd7f96
- hxxps://download-365[.]com/filedownload/download.php?u=033d4773-c8fd-405d-92ff-eec61edb6c75
- hxxps://download-365[.]com/filedownload/download.php?u=33560fe7-48d1-46b4-8a4b-1847f3071374
- hxxps://download-365[.]com/filedownload/download.php?u=befe7355-64c7-4be9-a700-5d85ee66a55e
- hxxps://download-365[.]com/filedownload/download.php?f=rtf-dwnxcr28tw974234&u=e7794864-36dc-4adc-8b1b-ebabb832b5c2
- hxxps://download-click[.]net/download/download.php?u=f195b4fb-b3cb-4549-b1c7-0f5c25d2cf90
- hxxps://365downloading[.]com/download-zip4/download.php?u=2e1edfe9-32b3-46a3-bac7-9a88a8d221c4
- hxxps://365downloading[.]com/download-doc3/download.php?u=8b001f5a-be0d-4eca-8190-6db8f8024532
Link names:
- materialy.zip;
- podgotovlennyye_materialy.zip.
COMMAND AND CONTROL CENTER (C&C):
185.38.151.11
Recommendations
• Beware of any emails that try to force you to open attachments or follow any links.
• Always be careful with any e-mails sent by individuals or organizations from whom you usually do not receive emails and also from those with whom you regularly communicate (the sender’s box can be fake or compromised).
• Follow the rules of «digital hygiene».